C++ Openssl Generate Aes 256 Key
| Documentation |
| #include <openssl/evp.h> |
- C Openssl Aes Example
- Openssl Aes 256
- C Openssl Generate Aes 256 Key Loader
- Openssl Aes 128
- Aes 256 Java
- Openssl Aes Decrypt C++ Example
Openssl aes-256-cbc -salt -a -d -in encrypted.txt -out plaintext.txt Asymmetric encryption. For Asymmetric encryption you must first generate your private key and extract the public key. Openssl genrsa -aes256 -out private.key 8912 openssl rsa -in private.key -pubout -out public.key To encrypt. Apr 27, 2016 Encrypt data using AES and 256-bit keys AES stands for Advanced Encryption Standard and is an industry-standard algorithm for encrypting data symmetrically which even the US government has approved for SECRET documents.
Jun 23, 2012 The AES key is much simpler; it’s just random data so we call RANDbytes to get the number of random bytes needed for the AES encrypted key and IV. There is also the option to use the EVPBytesToKey function which is a PBKDF. This function, as I called it, will generate a 256 bit key in CBC mode, with a salt and passphrase that are random. When you use openssl enc, you need to select a mode of operation in addition to the key size, e.g. Aes-256-cbc specifies the mode CBC with PKCS#5 padding. CBC specifies how to encrypt multiple 128-bit blocks, and PKCS#5 specifies how to pad the message to a whole number of blocks.) AES-256 requires a 256-bit key, period.
C Openssl Aes Example
The libcrypto library within OpenSSL provides functions for performing symmetric encryption and decryption operations across a wide range of algorithms and modes. This page walks you through the basics of performing a simple encryption and corresponding decryption operation.
In order to perform encryption/decryption you need to know:
- Your algorithm
- Your mode
- Your key
- Your Initialisation Vector (IV)
This page assumes that you know what all of these things mean. If you don't then please refer to Basics of Encryption.
The complete source code of the following example can be downloaded as evp-symmetric-encrypt.c.
Setting it up[edit]
The code below sets up the program. In this example we are going to take a simple message ('The quick brown fox jumps over the lazy dog'), and then encrypt it using a predefined key and IV. In this example the key and IV have been hard coded in - in a real situation you would never do this! Following encryption we will then decrypt the resulting ciphertext, and (hopefully!) end up with the message we first started with. This program expects two functions to be defined: 'encrypt' and 'decrypt'. We will define those further down the page. Note that this uses the auto-init facility in 1.1.0.
The program sets up a 256 bit key and a 128 bit IV. This is appropriate for the 256-bit AES encryption that we going to be doing in CBC mode. Make sure you use the right key and IV length for the cipher you have selected, or it will go horribly wrong!! The IV should be random for CBC mode.
We've also set up a buffer for the ciphertext to be placed in. It is important to ensure that this buffer is sufficiently large for the expected ciphertext or you may see a program crash (or potentially introduce a security vulnerability into your code). Note: The ciphertext may be longer than the plaintext (e.g. if padding is being used).
We're also going to need a helper function to handle any errors. This will simply dump any error messages from the OpenSSL error stack to the screen, and then abort the program.
Encrypting the message[edit]
So now that we have set up the program we need to define the 'encrypt' function. This will take as parameters the plaintext, the length of the plaintext, the key to be used, and the IV. We'll also take in a buffer to put the ciphertext in (which we assume to be long enough), and will return the length of the ciphertext that we have written.
Encrypting consists of the following stages:
- Setting up a context
- Initialising the encryption operation
- Providing plaintext bytes to be encrypted
- Finalising the encryption operation
During initialisation we will provide an EVP_CIPHER object. In this case we are using EVP_aes_256_cbc(), which uses the AES algorithm with a 256-bit key in CBC mode. Refer to Working with Algorithms and Modes for further details.
Decrypting the Message[edit]
Finally we need to define the 'decrypt' operation. This is very similar to encryption and consists of the following stages:Decrypting consists of the following stages:
- Setting up a context
- Initialising the decryption operation
- Providing ciphertext bytes to be decrypted
- Finalising the decryption operation
Again through the parameters we will receive the ciphertext to be decrypted, the length of the ciphertext, the key and the IV. We'll also receive a buffer to place the decrypted text into, and return the length of the plaintext we have found.
Note that we have passed the length of the ciphertext. This is required as you cannot use functions such as 'strlen' on this data - its binary! Similarly, even though in this example our plaintext really is ASCII text, OpenSSL does not know that. In spite of the name plaintext could be binary data, and therefore no NULL terminator will be put on the end (unless you encrypt the NULL as well of course).
Here is the decrypt function:
Ciphertext Output[edit]
If all goes well you should end up with output that looks like the following:
Serv-u mft server key generator. “Serv-U Managed File Transfer Server is a versatile, easy to deploy solution that integrates well into existing infrastructure meeting all our compliance requirements. Serv-U MFT Server supports two-factor authentication using passwords and a client key. Client keys can be generated using a built-in Serv-U MFT Server key generator, or imported from third-party solutions.
For further details about symmetric encryption and decryption operations refer to the OpenSSL documentation Manual:EVP_EncryptInit(3).
Padding[edit]
OpenSSL uses PKCS padding by default. If the mode you are using allows you to change the padding, then you can change it with EVP_CIPHER_CTX_set_padding. From the man page:
EVP_CIPHER_CTX_set_padding() enables or disables padding. By default encryption operations are padded using standard block padding and the padding is checked and removed when decrypting. If the pad parameter is zero then no padding is performed, the total amount of data encrypted or decrypted must then be a multiple of the block size or an error will occur..PKCS padding works by adding n padding bytes of value n to make the total length of the encrypted data a multiple of the block size. Padding is always added so if the data is already a multiple of the block size n will equal the block size. For example if the block size is 8 and 11 bytes are to be encrypted then 5 padding bytes of value 5 will be added..
If padding is disabled then the decryption operation will only succeed if the total amount of data decrypted is a multiple of the block size.C++ Programs[edit]
Questions regarding how to use the EVP interfaces from a C++ program arise on occasion. Generally speaking, using the EVP interfaces from a C++ program is the same as using them from a C program.

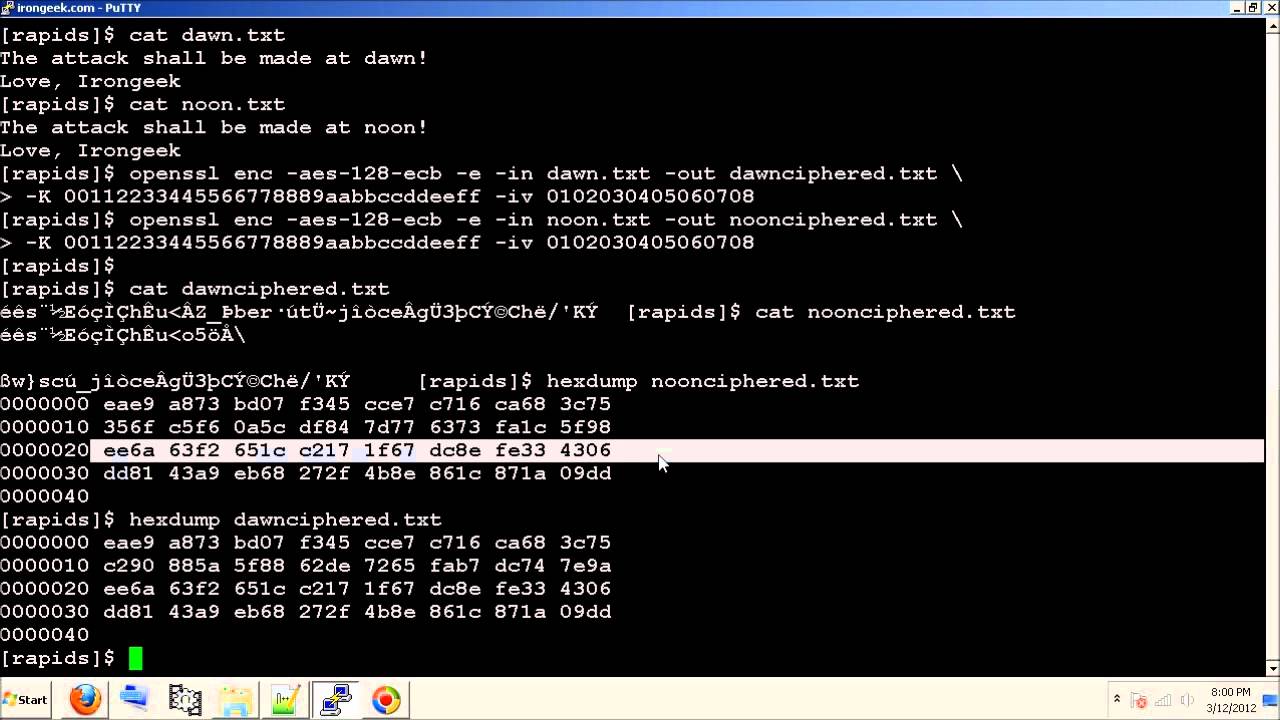
You can download a sample program using EVP symmetric encryption and C++11 called evp-encrypt.cxx. The sample uses a custom allocator to zeroize memory, C++ smart pointers to manage resources, and provides a secure_string using basic_string and the custom allocator. You need to use g++ -std=c++11 .. to compile it because of std::unique_ptr.
You should also ensure you configure an build with -fexception to ensure C++ exceptions pass as expected through C code. And you should avoid other flags, like -fno-exceptions and -fno-rtti.
The program's main simply encrypts and decrypts a string using AES-256 in CBC mode:
And the encryption routine is as follows. The decryption routine is similar:
Notes on some unusual modes[edit]
Worthy of mention here is the XTS mode (e.g. EVP_aes_256_xts()). This works in exactly the same way as shown above, except that the 'tweak' is provided in the IV parameter. A further 'gotcha' is that XTS mode expects a key which is twice as long as normal. Therefore EVP_aes_256_xts() expects a key which is 512-bits long.
Authenticated encryption modes (GCM or CCM) work in essentially the same way as shown above but require some special handling. See EVP Authenticated Encryption and Decryption for further details.
See also[edit]
OpenSSL is among the most popular cryptography libraries. It is most commonly used to implement the Secure Sockets Layer and Transport Layer Security (SSL and TLS) protocols to ensure secure communications between computers. In recent years, SSL has become basically obsolete since TLS offers a higher level of security, but some people have gotten into the habit of referring to both protocols as SSL.
Cryptography is tricky business, and OpenSSL has too many features to cover in one article, but this OpenSSL tutorial will help you get started creating keys and certificates.
OpenSSL tutorial: An introduction to internet security
When a client requests a secure connection to a server, the server, in turn, requests information to figure out which types of cryptographic security the client can support. Once it determines the most secure option, the following takes place:
- The server sends a security certificate that is signed with the server’s public key.
- Once the client verifies the certificate, it generates a secret key and sends it to the server encrypted with the public key.
- Next, both sides use the secret key to create two sets of public-private keys. At last, secure communication can commence.
SSL and TLS are two of many security protocols used to accomplish these steps. To implement these protocols, we need software like OpenSSL.
Abbreviations key
You’ll come across tons of abbreviations in this guide and other OpenSSL tutorials. For quick reference, here is a short list of some terms you might encounter:
- CSR: Certificate Signing Request
- DER: Distinguished Encoding Rules
- PEM: Privacy Enhanced Mail
- PKCS: Public-Key Cryptography Standards
- SHA: Secure Hash Algorithm
- SSL: Secure Socket Layer
- TLS: Transport Layer Security
Part 1 - Getting started
You can download the source code for most platforms from the official OpenSSL website.
If you need a windows distribution, Shining Light Productions has a good one although there are plenty of alternatives. Once everything is successfully installed, let’s begin by experimenting with the OpenSSL command line tool.
First, you can use the following command to display which version of OpenSSL you’re running:
To get a full list of the standard commands, enter the following:
Check out the official OpenSSL docs for explanations of the standard commands. To view the many secret key algorithms available in OpenSSL, use:
Now, let’s try some encryption. If you wanted to encrypt the text “Hello World!” with the AES algorithm using CBC mode and a 256-bit key, you would do as follows:
You’ll be prompted to enter a password from which the 256-bit secret key will be computed. In the above example, the password example is used, but you should have stronger passwords. You should now have a binary file called encrypted.bin that you can decrypt as follows:
Openssl Aes 256
Part 2 - Public and private keys
For the sake of example, we can demonstrate how OpenSSL manages public keys using the RSA algorithm. You can use other algorithms of course, and the same principles will apply. The first step is to generate public and private pairs of keys. Enter the following command to create an RSA key of 1024 bits:
You should now have a file called key.pem containing a public key and private key. As the file’s name suggests, the private key is coded using the Privacy Enhanced Email, or PEM, standard. Use the following code to display it:
You should see a long combination of characters. For detailed information about how your key was generated, enter:
This command should return information about the public and private exponents, the modulus and the other methods and numbers used to optimize the algorithm. In this context, the -noout option prevents display of the key in base 64 format, which means that only hexadecimal numbers are visible. The public exponent is an exception, of course, since it is always 65537 for 1024 bit keys.
To encrypt our private key, we use the following code:
Once the key file has been encrypted, you will then be prompted to create a password. Next, we can extract the public key from the file key.pem with this command:
Finally, we are ready to encrypt a file using our keys. Use the following format:
In the above context, <input_file> is the file you want to encrypt. Since we’re using RSA, keep in mind that the file can’t exceed 116 bytes. The <key.pem> is the file containing the public key. If that file doesn’t also include the private key, you must indicate so using -pubin. The <output_file> is the encrypted file name.
Now, to decrypt the file, you can simply flip the equation. Change -encrypt to -decrypt, and switch the input and output files.
Part 3 - Creating digital signatures
At last, we can produce a digital signature and verify it. Signing a large file directly with a public key algorithm is inefficient, so we should first compute the digest value of the information to be signed. This can be accomplished using the following command:
In this example, <hash_algorithm> is whichever algorithm you choose to compute the digest value. The <input_file> is the file containing the data you want to hash while “digest” is the file that will contain the results of the hash application.
The next step is to compute the signature of the digest value as follows:
Ssh generate key without passphrase id. Finally, you can check the validity of a signature like so:
Here, signature is the filename of your signature, and key.pem is the file with the public key. To confirm the verification for yourself, you can compute the digest value of the input file and compare it to the digest value produced from the verification of the digital signature.
Part 4 - Certificate signing requests
Let’s say that you want to create digital certificates signed by your own certificate authority. Before you can get an SSL certificate from a certificate authority, or CA, you must first generate a certificate signing request or a CSR. A CSR includes a public key as well as some extra information that gets inserted into the certificate when signed.
When you first create a CSR, you’ll be asked to supply some information about yourself or your organization. In the field “Common Name,” or CN, you must provide the fully qualified domain name of the host for which the certificate is intended. If you’re actually purchasing an SSL certificate from a CA, then the information you provide should be factual and accurate! Imagine you want to secure an Apache HTTP or Nginx web server with HTTPS. You can use the following snippet to create a new 2048-bit private key along with a CSR from scratch:
Imagine you want to secure an Apache HTTP or Nginx web server with HTTPS. You can use the following snippet to create a new 2048-bit private key along with a CSR from scratch:
Just replace “domain” with your domain name. Here, the -newkey rsa:2048 option tells OpenSSL that it should use the RSA algorithm to create a 2048-bit key, and the -nodes option indicates that the key shouldn’t be password protected.
After you’ve provided all of the necessary information, your CSR will be generated. Now, you can send it to a CA and request an SSL certificate. If your CA supports SHA-2, be sure to add the -sha256 option if you want your CSR to be signable with SHA-2.
To create a CSR for a private key that already exists, you would use this format:
Again, replace domain with your domain name. The -key option here indicates that you’re using an existing private key while -new indicates that you’re creating a new CSR. In the prior example, -new was implied because you were making a new key.
Let’s say you already have a certificate that you want to renew, yet you somehow lost the original CSR. Don’t panic; you can generate a new one based on information from your certificate and the private key. For example, if you were using an X509 certificate, you’d use the following code:
The -x509toreq option is needed to let OpenSSL know the certificate type.
Part 5 - Generating SSL certificates
If you desire the extra security of an SSL certificate, but you can’t afford or don’t want to be bothered with a CA, a less expensive alternative is to sign your own certificates. Self-signed certificates are signed with their own private keys, and they are just as effective at encrypting data as CA-signed certificates; however, users might receive an alert from their browser indicating that the connection is not secure, so self-signed certificates are really only recommended in environments where you’re not required to prove your service’s identity such as on a non-public server.
Again, assume that you’re using HTTPS to secure an Apache HTTP or Nginx web server. The following command will create a 2048-bit private key along with a self-signed certificate:
The -x509 option tells OpenSSL that you want a self-signed certificate, while -days 365 indicates that the certificate should be valid for one year. OpenSSL will generate a temporary CSR for the purpose of gathering information to associate with the certificate, so you will have to answer the prompts per usual.
C Openssl Generate Aes 256 Key Loader
If you already have a private key that you want to associate with a self-signed certificate, just change the code slightly:
Remember that inclusion of the -new option is necessary since you are creating a new CSR from an existing key.
Part 6 - Viewing certificates
To view certificates and CSR files, you must decode them from the PEM format. Use the following command to view the contents of a CSR in plain text:
To view a certificate’s content in plain text, use:
Openssl Aes 128
You can verify that a certificate was signed by a specific CA by plugging its name into the following code:
Aes 256 Java
Summary
In today’s increasingly digital world, improving internet security is imperative to protect our own security. Many website databases contain treasure troves of information about visitors, and hackers are always learning new ways to navigate system vulnerabilities and exploit such data. That’s why security protocols must continue to evolve. Stay informed to make sure you’re providing adequate protection for your users.
Openssl Aes Decrypt C++ Example
- Share